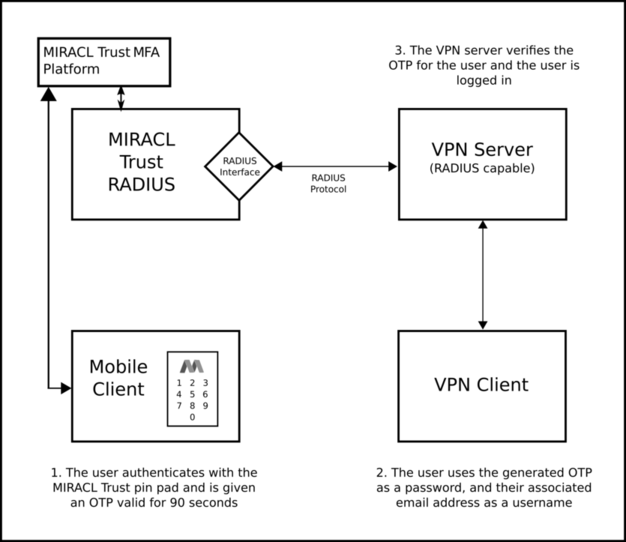
MIRACL Trust RADIUS is a RADIUS server implementing authentication, authorization and accounting. It could be configured to communicate with one or more RADIUS-supporting clients so they gain access to a particular network resource using One Time Passwords (OTPs) generated from the MIRACL Trust authentication platform. You could generate OTPs either by visiting your saved OTP url in your web browser or by your mobile app connected to the MIRACL Trust authentication platform. They are valid for a default of 90 seconds. MIRACL Trust RADIUS could be configured to authenticate using one of the following authentication mechanisms - PAP, CHAP, MSCHAPv1 and PEAPv0-MSCHAPv2 which allows you to authenticate through a secure tunnel.
Once installed, the use of MIRACL Trust RADIUS involves managing a set of config
files which are located in the /etc/miracl-radius/ directory.
The steps involved are:
-
Register in the MIRACL Trust portal and create a new MIRACL RADIUS Server App. You can generate an OTP by its Registration and OTP Generation Link following this guide.
-
Install your MIRACL Trust RADIUS server.
-
Configure your MIRACL Trust RADIUS server and RADIUS client / VPN server (simple ssh client, OpenVPN, Cisco Anyconnect etc.).
-
End users can then visit the OTP generation url in their browser or use the MIRACL Trust mobile app to generate One Time Passwords (associated with the same email they registered with in step 2) which allow them to log in to the RADIUS client / VPN server with the registered user identity and the generated OTP as a password.
# Server Configuration
The configuration of MIRACL Trust RADIUS server is managed using config files
stored in the /etc/miracl-radius/ directory. The functions served by these
files can be split into separate files and then loaded by the main config.yaml
file which lists the files to be loaded as ‘includes’. The config.yaml file
could include all of the configuration itself in one large file, but it is
recommended to split and name the files into a logical structure that enables
more modular management of functionality and Hosts. Note that MIRACL Trust
supports config files in both YAML and JSON format. Throughout the
documentation, however, we are using YAML.
Note that the default example layout and naming of the config files are only for
guidance, and you can choose a different structure and naming system and
describe it in the include section of the main config.yaml file.
/etc/miracl-radius/
├── config.yaml
├── core.yaml
├── hosts
│ └── example.yaml
│ └── fortigate.yaml
│ └── openvpn.yaml
│ └── sshtest.yaml
└── integrations
├── accounting.yaml
├── ldap.yaml
├── log.yaml
├── peap.yaml
├── redis.yaml
├── stats.yaml
└── mfa.yaml
The config.yaml file simply lists the other files to be included. The
following example shows that you are only including core.yaml
hosts/openvpn.yaml and integrations/ldap.yaml:
includes:
- core.yaml
# - hosts/example.yaml
- hosts/openvpn.yaml
# - hosts/sshtest.yaml
# - integrations/log.yaml
- integrations/ldap.yaml
# - integrations/mfa.yaml
# - integrations/peap.yaml
# - integrations/redis.yaml
# - integrations/stats.yaml
core.yaml contains the basic details of your MIRACL Trust RADIUS installation, plus the Client ID and Client Secret obtained from the admin portal.
In the hosts/ subfolder, you can configure multiple hosts for OTP access (ssh clients, VPN clients, etc.).
LDAP and other advanced settings can be configured in the integrations/ subfolder. More information on this can be found in the LDAP and authorization section and in the Advanced config section.
Note that settings in files lower down the list of includes overrides the settings in those higher in the list. For example, if you include a file which specifies a server port number, this overrides a server port number set in a file higher in the list of includes.
When changes have been made to your MIRACL Trust RADIUS config files (in the
/etc/miracl-radius/ directory), it is necessary to restart the service so
changes can apply.
An explanation of making necessary configurations is found in the Generic client setup info and SSH demo and OpenVPN demo pages.
# Component Diagram
The following diagram gives a high-level overview of the components involved: