Microsoft’s Active Directory Federation Services (ADFS) is an Identity Provider (IdP) providing Single Sign-On for supporting client applications (e.g. Office365). ADFS authenticates users against an Active Directory instance and, optionally, a third-party MFA provider can be configured to provide an extra layer of authentication for added security. The MIRACL Trust ADFS authentication provider is a plugin which enables you to use the MIRACL Trust OIDC-based authentication platform as such a third-party MFA authentication provider for ADFS. The plugin is deployed on each ADFS server using a simple installation package, and does not require the installation of any other on-premise MIRACL services. It is then configured through the standard ADFS administration interface. The plugin doe not provide or require any additional network endpoints and therefore no changes need to be made to incoming firewall rules. The plugin requires outgoing access to request the following urls: https://api.mpin.io/oidc/certs, https://api.mpin.io/oidc/token and https://api.mpin.io/.well-known/openid-configuration. The following diagram gives a high-level overview of the components involved:
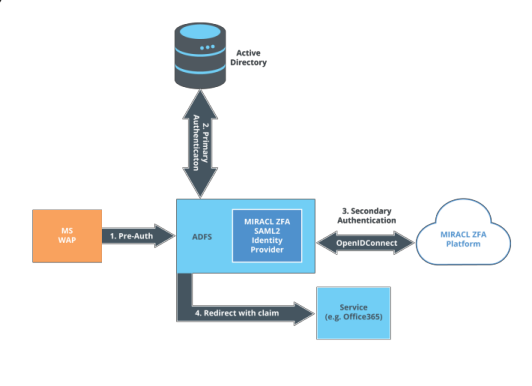
In order to setup the plugin, the following steps must be taken:
In the following instructions it is assumed that an ADFS server / server farm and a proxy (e.g. MSWAP) are set up and running as your organisation requires (https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/deployment/windows-server-2012-r2-ad-fs-deployment-guide). It is also assumed that any client applications (e.g. Office365) are already working with your ADFS instance.
-
Create a new app in the MIRACL Trust portal which gives you a client id and client secret to enable authentication with the MIRACL Trust service (https://trust.miracl.cloud)
-
Run the MIRACL Trust ADFS plugin installer, entering the client id and client secret for your app when prompted. On a server farm, this must be run first on the primary ADFS server, then on each of the secondary servers without entering the client id and client secret again (the procedure for this varies slightly depending on whether you are running a standard / WID setup or a SQL setup)
-
Activate the plugin in ADFS using the ADFS administration interface
-
Configure users in Active Directory (Please note that in the MFA platform all identities are converted to lowercase. Hence, if you assign an email containing uppercase characters to a Windows user in Active Directory the user will be required to authenticate with the lowercase equivalent. For example John.Smith@example.com will need to authenticate as john.smith@example.com)
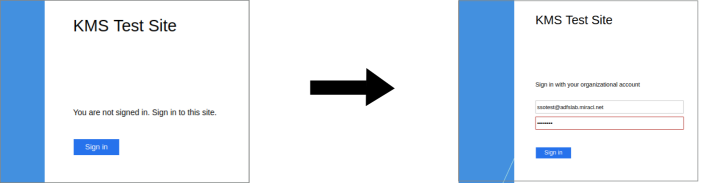
When users then access a configured client application, they will be guided through a two-step authentication process:
-
The Primary Authentication phase, whereby they will enter their Active Directory username and password.
-
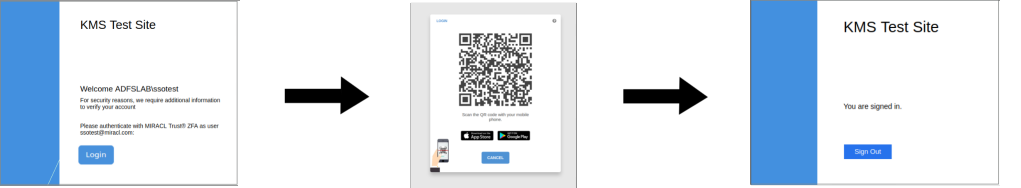
The Multi-Factor Authentication phase, whereby the MIRACL Trust service will deal with final authentication of the user. At this point the user will be presented with a QR code which they can scan with their mobile app before entering their PIN to authenticate.
-
The user’s browser is then redirected back to the client application, and they are logged in.